Understanding Technology, Methods and Authentication
Electronic signature or e-signature is a technology for signing electronic document files with a handwritten signature in electronic form. This technology allows complete elimination of the document mailing, filing, storing, copying and retrieval of paper documents. Thus saving much of your business time and money.
As businesses are moving towards a paperless workplace and substituting them with more efficient and cost effective electronic options, e-signature technology has become a very important part of investment for the regular utilisation. This cost and time saving option for doing business electronically is evident, yet many companies are still choosing which technology or method is best suited to their needs. Creating, signing, transmitting, and storing all documents electronically and in such a way that it is legally-binded can seem like a daunting task.
What is an electronic signature?
"Electronic Signature" can be illustrated as the signature in digital form which is attached to other electronic data that serves as a method of authentication of an electronic document.
With the signotec software you can produce legal "advanced electronic signatures" according the directive of the European Parliament and of the council.
An electronic signature which meets the following requirements:
a) it is uniquely linked to the signatory;
b) it captures the identity of the signatory;
c) it is manufactured using such technology that the signatory can maintain under his sole control; and
d) it is linked to the sign to which it relates in such a manner that any subsequent change of the signature is detectable.
According to the stipulations, several different methods and technologies for using digital signature on a document. There are two standard types of e-signature technology that are widely used however both differ in substance such as PIN/Password signature stamps, Public Key and digitised handwritten signatures.
A PIN/Password stamp inserts a single fixed signature image into each signed document when a user types a password or PIN. The digitised handwritten signatures are captured with special pen and tablet technology that transforms the user's signature precisely into pen events or an image. All the methods have different consequences for security and authentication.
Why to avoid PIN/Password and PKI Signatures
Companies that provide PIN signature stamps may claim their technology is legally pliable as it qualifies as an "electronic sound process", however, it does not satisfy the points enumerated above. In case of PIN signature stamps each and every signature is identical in its form and composition, just like a signature made out of a rubber stamp. It does not record a person's signature rather it is result of the particular password entered.
If a forensic examiner views the signature, they cannot determine the origin of the signature image as it is password or PIN that could be typed by anyone. Authentication is the point that the PIN or Password signature stamps falls short for hence they can be fraudulent. For these reasons, the advanced electronic signature technology are recommended for all business to invest in, so that each and every signature recorded is unique and relying on "rubber stamp" technology is a risky factor.
PKI digital signatures and certificates are simply a more complex version of PIN signature technology, in which a larger (often 128-bit) encryption number is used, meaning it is too large to be remembered and typed. Portability is also limited because the key is permanently linked to a host computer, or a “secure” smart card which can be lost, stolen or hacked.
Using Handwritten Electronic Signatures
The Handwritten Electronic Signature is a better choice for digital signature market, especially with the great options of hardware and software. Even if you consider digital signature technology to be best for replacing traditional methods of signing, there are several points to be considered while choosing a system for your business. The signature hardware manufacturers maintain the specifications, data format and software systems that affects the security, authentication and legality of the signature.
Signature Security
An electronic signature to be valid under the national ESIGN electronic commerce law, it must maintain the privacy and legal enforceability and remain under the “sole control of the signer”. To fulfil the requirement, an e-signature must be linked or attached to the relevant document directly with no infiltrator or copies. Binding the document in such a way will satisfy the security feature as to render document tampering detectable. In absence of these important features, it is not possible to detect the tampering of the signature in the document that was identical in form to the state in which it was initially signed. There is no substitute for an effective security policy which prevents viruses, worms and data sniffers from residing on a client or server computer. Encryption gimmicks in a signature pad connected to a PC provide a false sense of security if a rogue program or keyboard, printer, screen, memory, or USB data sniffer is also on the PC. Matters can be made worse if overly powerful and un-necessary processors and operating systems are employed in electronic signature devices, due to latent bugs and viruses or internal data storage and encryption; as these techniques further jeopardize and remove security monitoring and update capability from the hands of IT personnel.
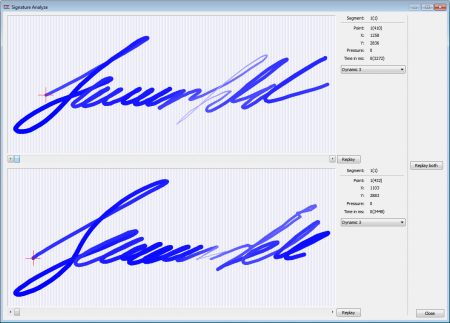
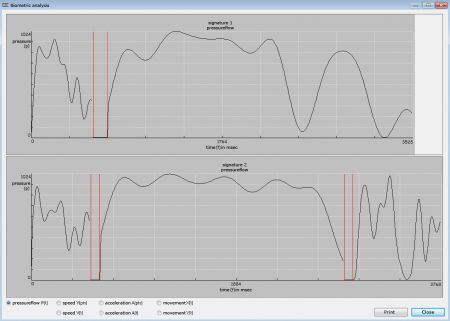
On the other hand, there is value in monitoring and evaluating the integrity of data received from a signature pad, such as the point sampling rate, and detection of unusual time-related activity in signing which may indicate an attempt to trace or forge a signature (slow-signing effect). This capability is described further in US Patent 6,307,955.
Document security and signature binding are also very important. Hence, if the signature is not attached to the document properly, it has no real value since there would not be any proof of tampering made to the terms post signing. The forensics can perform several tests using infrared, ultraviolet and microscopic inspection in the paper based world, to determine the tampering in the signature, however in the electronic realm, this is attained using a cryptographic hash and binding system, and notify signature as "lost" if the contents are altered.
Signature Authentication
A significant feature of handwritten signatures (ink-on-paper) is that they can studied and analysed by forensics handwriting experts and then compare them with existing signatures for authentication. Hence, the most challenging characteristics is the validity and authentication of the e-signature, since only few providers support their technology with verification tools. If the signature cannot ne attributed to the attached signatory, it is worthless. E-signatures are not exceptions and require authentication and verification to be valid and binding. Every technology provider must have authentication tools and training in-place before selecting their solution.
Systems that embed a signature in the form of image into an electronic document (whether via PIN or biometric input) are less accepted legally than faxed or photocopied signatures. Just like a PIN/Password signature system, the object representing the signature is a superficial representation with no data linking the image to a biometric performance, and unlike a fax transaction, there is no 3rd-party record of the transmission. A bitmap, tif, or jpg image is not useful to a forensic examiner as it provides no detailed characteristics for analysis as is provided with original pen data.
The most accurate, reliable, and secure method of capturing a signature is in the form of raw pen events. A file of this type contains no images or analysis of the signature, just the pen events and position converted at high speed. This data has the additional advantage of being stored in a database or bound to the contents of a document very securely since it does not exist as a common image file format. It cannot be easily copied or viewed and used as a reference for forgers since there is no embedded image. Furthermore, since all original captured pen events are present in the e-signature itself, a forensic expert can later examine it point-by-point using specialised signature analysis software, if available.
Understanding Biometrics and Authentication
Another issue to be considered with handwritten digital signature is the type of biometric data, if any, that is captured and stored in a signature file. Pen pressure management is an essential element. Pressure is an unreliable biometric measurement due to the level of uncertainty inherited from one signature to another. The level of pressure a signature pad senses for a single person will vary widely based on height and orientation of the signatory to the sensor, the person’s mood, time of day, angle of the pad, size of the pen or stylus, calibration of the software, sensor age and wear, etc. As a result, a pressure-oriented primary biometric is susceptible to unnaturally high false-negative responses when automated or independent validation is attempted. In other words, when pressure is used to determine the validity of one or more signatures, it is far more likely to be a cause for rejection than for authentication, even if the signatures were created by the same user. Drastic variance makes signatures difficult to authenticate, even if they are valid.
Make sure that the technology provider offres software for signature authentication or else there would be legal challenges ahead. Several software providers offer automated template-based validation, but this technique is often not a viable option for post-signature back-end authentication. Examiners cannot independently verify the signature. It also requires each user to offer enough signatures to create a sample template, which is unwieldy, especially in a one-time customer interaction in a bank, pharmacy, or mortgage lender’s office. While automated validation software has many useful applications, be sure to choose a technology which is supported by independent forensic authentication tools. Many technology providers promise true biometric signatures, but lack the authentication tools to make their signature data forensically significant.
Conclusions
In general, while deciding the e-signature system, choose the device best suiting your business. If a technology uses or matches these features then it is probably a safe and reliable option. A system is to encounter difficulties and fraudulent practice, if a system employs more technical shortcuts, such as creating multiple signatures with one stroke of a pen or keypad, or saving flat images in place of real, forensic-quality signatures. With old ink-on-paper characteristics as your guide, your electronic document solution should be a signature success.